Featured
By expanding broadband access and investing in America’s future, we can open a bridge to possibility for all.
Search
Filter
Location
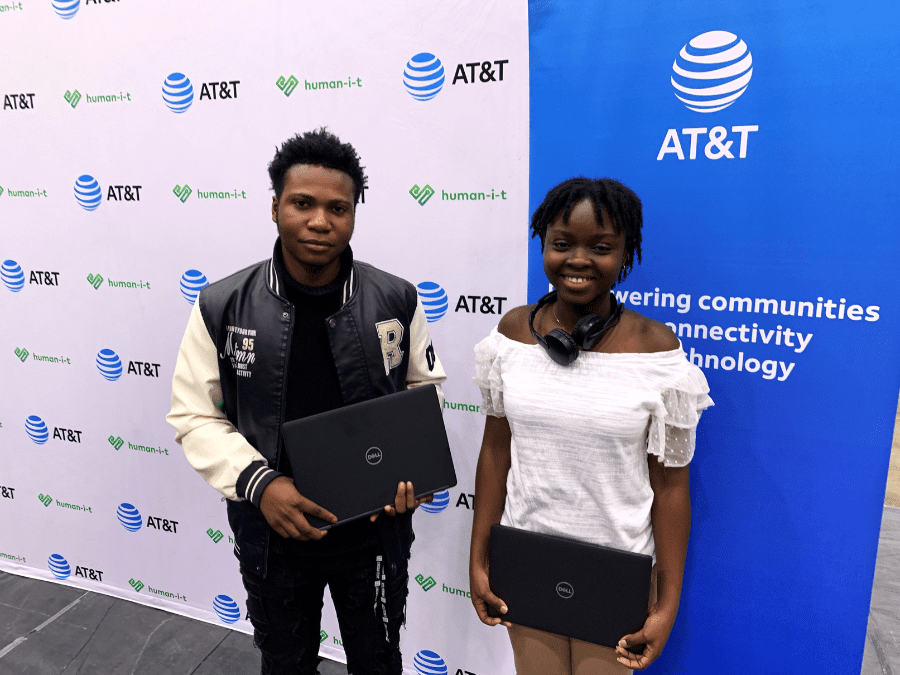
Helping Indianapolis Students Connect in A ‘Very Digital World’
- Broadband Access and Affordability, Community Impact
- |

‘Making Life Accessible to People’: Grand Rapids’ Sonja Forte is Helping Bridge The Digital Divide
- Broadband Access and Affordability, Community Impact
- |

This Chicago Professor Emphasizes the Power of Connectivity
- Community Impact
- |

Connecting Rincon College Students to a Brighter Future
- Broadband Access and Affordability
- |

AT&T Celebrates International Girls in ICT Day 2024 in Slovakia
- International External & Regulatory Affairs
- |

Helping Customers Adjust to the End of ACP
- Broadband Access and Affordability
- |
